These instructions provide steps-by-step instructions for UV Hub and UV Tracks servers installation on Amazon Web Service (AWS) cloud services platform.
System Requirements
Deploying UV Hub system on AWS requires the following data and services:
- Computer with internet access and Mission Planner or QGroundControl GCS installed.
- Amazon Web Services account.
- Activated RockBLOCK Mk2 or RockBLOCK 9603 Iridium satellite communication module, if ISBD channel will be used.
Installation
Follow these steps to deploy UV Hub and UV Tracks servers on AWS:
- Open AWS Console and select the AWS region.
- Create a key pair in EC2 service.

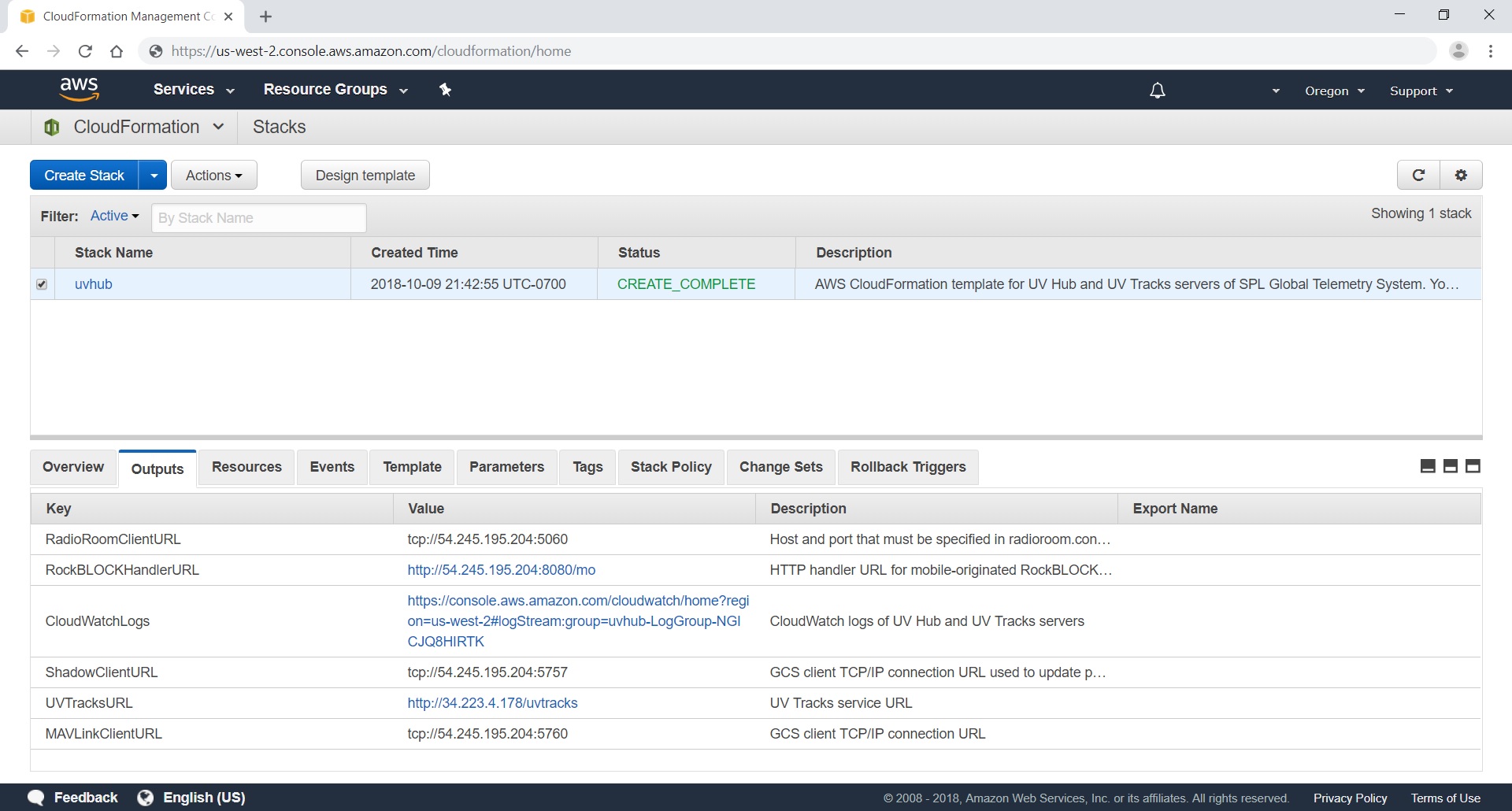
- Enter the RockBLOCK IMEI, Rock 7 user name and password, and other CloudFormation stack’s input parameters. Select the key pair name in the KeyName input parameter drop-down list. Make sure that values of
MAVAutopilotandMAVTypeinput parameters match your autopilot firmware. - Complete the stack creation wizard and wait until the stack creation is completed. Once the stack creation is successfully completed, the stack output parameters will be available.
- Register URL specified by
RockBLOCKHandlerURLoutput parameter as delivery address in Rock 7 Core services for your RockBLOCK. - Use the IP address and port number specified by
RadioRoomClientURLoutput parameter to sethostandportconfiguration properties of [tcp] configuration section in radioroom.conf UV Radio Room configuration file. - Connect the GCS to the autopilot using regular radio-telemetry or USB connection and save the on-board parameters to a file.
- Connect the GCS to the IP address and port number specified by
ShadowClientURLoutput parameter and upload the on-board parameters from the file to the vehicle. (This will update the parameters in the vehicle shadow.)
By default, the stack creates two EC2 instances of t2.micro type. t2.micro instances are eligible for AWS free tier. The stack also creates AWS Elasticsearch service instance of t2.small.elasticsearch type.
Tightening Security
By default ports 5760 and 5757 can be accessed from any client IP address. That is anybody who knows IP address of UV Hub server can connect to it and control your vehicle. To make these ports accessible just from your machine, Specify the client CIDR using ClientCIDR stack’s input parameter, or after the stack is created, change the in-bound rules for ports 5760 and 5757 in the EC2 security group created by the stack. Determine the public IP address of the GCS machine (http://checkip.amazonaws.com/) and set the source IP address for the ports to <IP address>/32. Make sure that the security group in-bound rules are updated whenever the GCS clients IP addresses are changed.
Access to port 8080 is used for delivery of mobile originated messages from RockBLOCK is restricted to originating IP addresses 109.74.196.135 and 212.71.235.32 of Rock 7 services.
Controlling access to port 5060 used by TCP/IP connections from UV Radio Room based on IP address ranges is not practical. Cellular internet providers will typically use dynamic IP addresses those may be reassigned on reboots. To secure UV Radio Room to UV Hub TCP/IP communication it’s recommended to use VPN remote-access solutions (for example, see Software Remote-Access VPN).
Troubleshooting
CloudWatchLogs stack output parameters links to the CloudWatch log group with UV Hub and UV Tracks servers logs.